We live in what has been called the information age. Undoubtedly, we today are the most connected and informed generation of human history. At the flick of a finger, we can get access to a plethora of information regarding almost any subject that we’re curious about.
Data has been curated not just about the things around us but from them as well. A whole industry has emerged over time whose primary goal is to extract data from the most basic to the most complex sources, and to then convert that data to valuable information.
This industry is the Internet of Things (IoT). At the core of the IoT industry sit various technologies that make it possible for data to be transmitted from one source to another. One of these technologies is a technology called Bluetooth. Undoubtedly, many millions of people are familiar with Bluetooth as it is so embedded in our everyday life.
However despite this, not many are familiar with how Bluetooth functions and what is actually going on when we connect our devices. The goal of this article is to allow readers to have a look under the hood in order to understand how the Bluetooth on their devices is working.
Bluetooth Classic & BLE
Bluetooth is a wireless technology used to pass data between two devices via radio waves. Over time, as Bluetooth as a technology matured and more devices were set up to use it, it became evident that there were various use-cases that the contemporary/classic version of Bluetooth was not able to address. As a result, BLE (Bluetooth Low Energy) was created. BLE was designed to significantly reduce the power consumption of devices as they communicated via Bluetooth. It accomplishes this by greatly reducing the amount of time that the Bluetooth radio is on.
This key change made it possible for devices to utilise Bluetooth for significantly longer periods of time without requiring a recharge. This feature was and is key for IoT because often in an IoT system, there will be hundreds of embedded devices transmitting constant streams of data. Therefore having the ability for these devices to run for longer without needing to be recharged or replaced greatly reduces not only cost but maintenance effort as well.
Roles & Responsibilities
In order to understand what’s going on any time Bluetooth is being used, it’s important to know and understand the roles and responsibilities of the two devices that are connected. With every Bluetooth connection, there are two roles that are being played out and these are: the central and peripheral roles. One device is the central device (or some may call it the server) and the other is the peripheral device (some may call this the client).
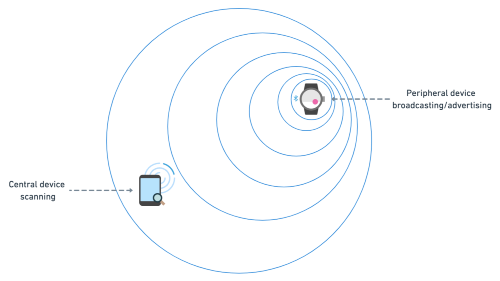
When a Bluetooth connection is about to be set up, one device (the peripheral) will advertise/broadcast information about itself to any devices near enough to pick up that broadcast. At the same time, somewhere nearby, a second device (the central) will be performing a scan and listening for any devices that are broadcasting.
As soon as the second (central) device picks up the advertising/broadcast information from the first (peripheral) device, an attempt to connect the devices will ensue (sometimes this requires human input — selecting one of the Bluetooth devices from a list of available/broadcasting devices).
Once a connection is established, the broadcasting device retains the role of the peripheral and the scanning device retains the role of the central. The peripheral device is responsible for outlining the type of data that it has available to offer and the central device then selects/interacts with the provided subset of data. The peripheral device does this by exposing its capabilities (what data is has on offer) to the central device by means of what are called ‘services’.
Services, Characteristics & Payloads
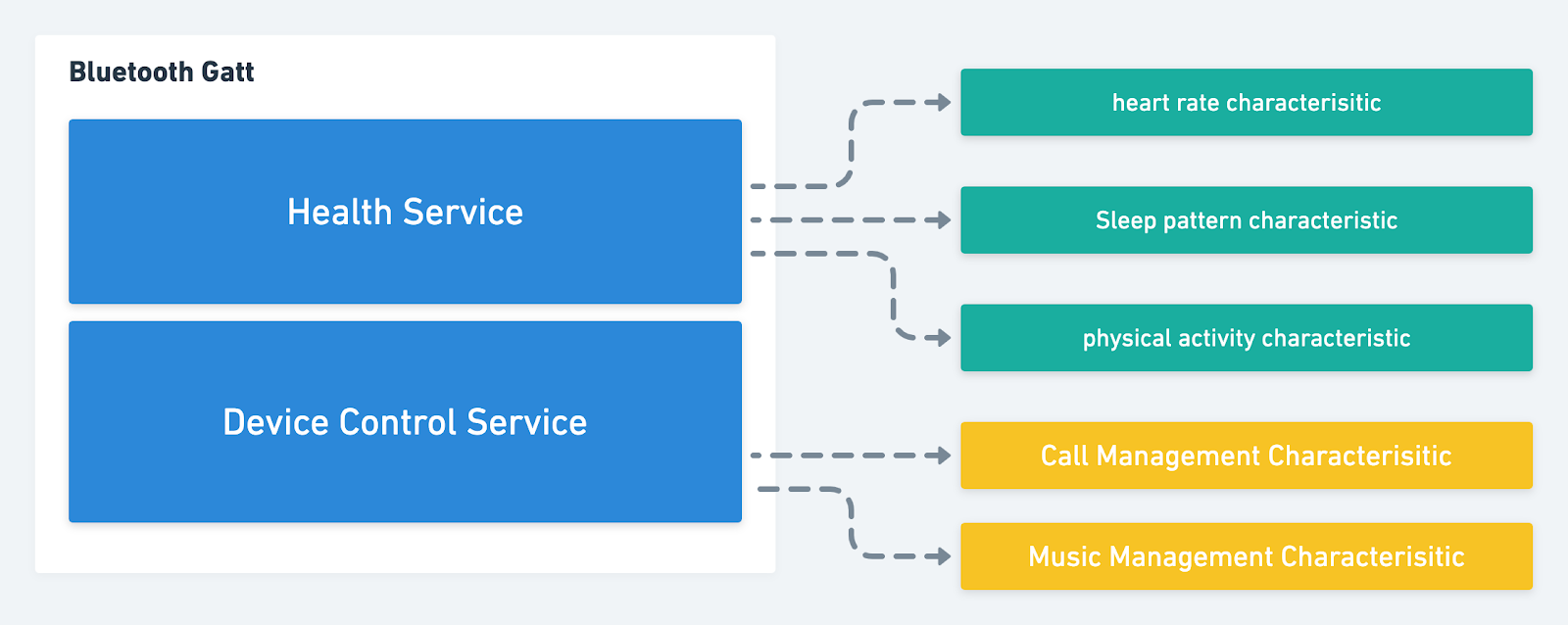
So what then is a service? A service is a grouping of related capabilities. For example, an apple watch may be able to control the pausing, stopping and playing music on the iPhone as well as the ability to answer and end calls. These two capabilities would exist in a single service called, for the sake of this article, the device control service.
The apple watch would also be able to pass information to the iPhone regarding the user’s physical activity, sleep patterns, heart rate, etc. These capabilities would exist on a different service, which we will call, the health service. By grouping capabilities in this way, the central device allows the peripheral device to quickly find, select and interact with the services it cares about.
Within each service will exist a list of characteristics. Each one of these characteristics represents a unique capability of the central device. If we were to use the previous example of the health service, it (the health service) would have three characteristics.
One for the sleep pattern detection capability, another for the heart rate detection capability and finally one for the physical activity detection capability. Once the peripheral device discovers these characteristics, it can write information to, request information from and subscribe to updates from these characteristics.
The actual mechanism for transmitting data between the two connected devices is what is called a byte array, the colloquial term of which is a payload. This is the packaging that the data is wrapped in as it moves from one device to another.
Read, Write & Notify
There are three ways by which data can be passed between the two connected devices, these are by means of reading, writing or notifying. The peripheral device can perform what is called a read. This would basically be the peripheral device asking the central device for a specific subset of data. An example of this would be an iPhone asking the apple watch for the user’s movement/physical activity data when the user opens the health app on the iPhone.
The central device can also, without request, offer information to the peripheral device by means of a notification (the peripheral device would need to be set up to listen for notifications). An example of this would be the apple watch alerting the user when their iPhone goes out of range.
Finally, the peripheral device can cause a change to occur on the central device by performing a write.
Once again, if we were to use the example of the apple watch and the iPhone, an example of a write would be the iPhone setting up the apple watch password. The user would type the password into the phone and then that password would be transmitted/sent to the apple watch. But what about security? Is it actually safe to send any data, let alone, sensitive data, like a password, via Bluetooth from one device to another (the iPhone to the apple watch)?
Security
A major concern for all connected systems, regardless of means of communication (http, Bluetooth, etc) is security. How can the system make sure that a malicious actor does not listen in to the communication between two devices or take control of one of the devices? The way BLE handles this concern is by encrypting the data that is passed between the two devices. BLE use AES encryption, which is the industry standard for data security. It uses the Elliptic Curve Diffie Hellman (ECDH) for generating public and private keys that are then used to encrypt and decrypt outgoing and incoming data.
What this means is that all data in transit (i.e, the apple watch password being sent) will be encrypted and only the device that knows how to decrypt it will be able to see it (once it’s decrypted of course). This security layer gives confidence not just to manufacturers who use Bluetooth in their hardware but also to everyday consumers who utilise the technology for various purposes, private and otherwise, in their everyday lives.
Conclusion
Bluetooth as a technology has advanced so much and looks like it will keep doing so. As technologies, such as Bluetooth advance and as more and more data is aggregated both from and about the environment around us, man will become more and more informed and connected to the environments that he lives in.
By Joseph Magara, Mobile Developer at GrowthOps
GrowthOps is a full-service digital agency that offers end to end digital marketing services such as Google Ads, Social Media, Partnership Marketing, and more. Speak to us about your growth needs today.